Introducing Catspin - The Power of Cloud in Pentesting
Cloud technologies and their special properties, if used creatively, can expand the pentester arsenal considerably. In some cases, they can render a lot of defensive strategies pretty much useless. Unfortunately, not a lot of people realize this, or know how to leverage the power that is contained in cloud tools for pentesting purposes, yet. In this post I will demonstrate this on the example of my recently developed Amazon API Gateway proxy tool, named catspin (see github). Catspin rotates the IP address of HTTP requests making IP based blocks or slowdown measures ineffective.
Block the IP address
In order to detect and block, for example, a possible directory scan, many security systems look for consecutive requests coming from the same IP address. The basic premise is: If the same IP address requests 20 different webpages in half a second it is probably not a legitimate user and more likely an automated scan. In such a case a defense strategy might slow down the traffic from this IP address or block it entirely.
This was never a really solid strategy as professional pentesters and hackers have access to proxy systems, so blocking a single IP address often did not have the desired effect. Getting blocked by a Web Application Firewall during a Burp scan is surely an experience many pentesters had. In such a case, you can switch IP addresses and go again, or you can scan slower or sneakier, e.g., by rotating your user agent. In case you have absolutely no idea what you’re doing, you can ask the customer to make an exception for the “pentester” and place the scanning IP address on the allow list :)
The power of cloud
Even though, if you knew what you’re doing, scanning sneaky or getting a new IP address in case you were blocked was never really tricky, it was still annoying. However, by creatively combining an HTTP proxy with the Amazon API Gateway service from AWS, none of this is necessary.
API Gateway is a highly flexible scalable and serverless API solution, which “acts as a ‘front door’ for applications to access data, business logic, or functionality from your backend services, such as workloads running on Amazon Elastic Compute Cloud (Amazon EC2), code running on AWS Lambda, any web application, or real-time communication applications.” (see https://docs.aws.amazon.com/apigateway/latest/developerguide/welcome.html)
The so called “front door”, simply put, is what your target sees and it comes from a pool of (different) legitimate AWS IP addresses.
Spin me right round baby right round
By using this native IP rotating feature of API Gateway and combining it with a REST API, which uses the ‘X-Forward-To’ HTTP header to forward its requests, catspin effectively rotates its IP address during scanning. For example, a directory scan using the tool dirsearch would look like this in the webserver-logs of a target:
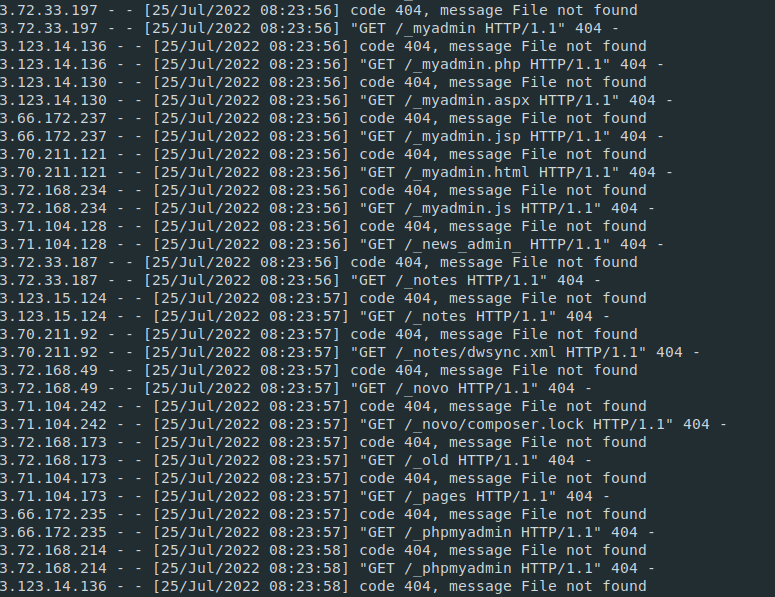
Obviously blocking one or more of these IP addresses does not impact the scan, and also simply blocking legitimate AWS IP addresses might not at all be a good idea for a company in the long run.
With the use of AWS CloudFormation, catspin can be deployed in your own AWS account within under one minute per target, and deleted if it is not needed, so it will not accumulate any charge while unused. Because catspin acts as proxy for all your HTTP requests it can perform directory scans via any tool that enables them, including wfuzz, gobuster, dirbuster etc. Additionally, many other vulnerability scanning tools request specific files via HTTP to determine software versions. Meaning catspin can also be utilized with tools like wordpress or typo3 vulnerability scanner. (see also Typo3 and Wordpress - in german language)).
How to install and deploy catspin can be found here -> github catspin